发表
2025
-
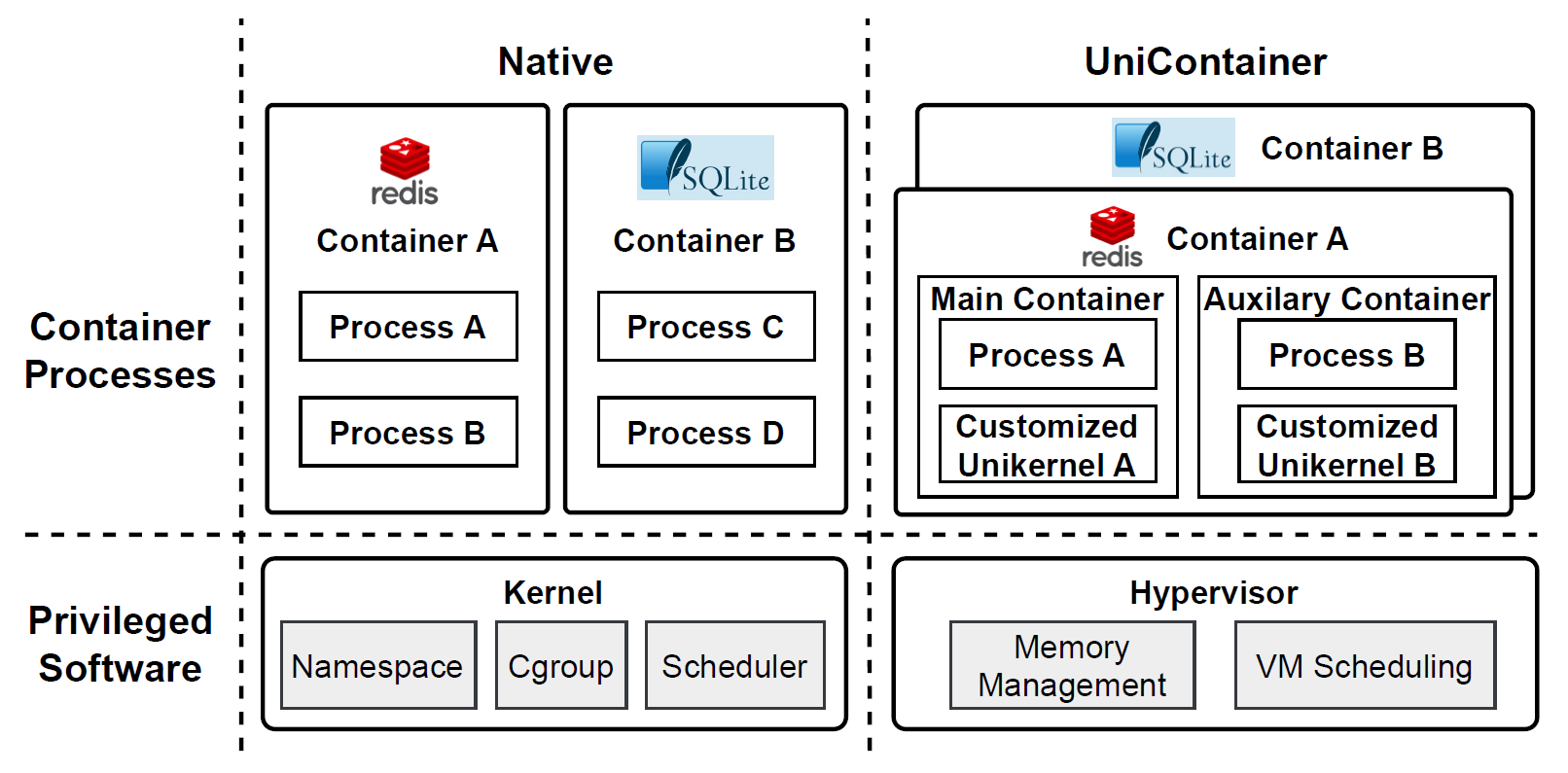 Unicontainer: Unlocking the Potential of Unikernel for Secure and Efficient ContainerizationContainer VirtualizationACM SIGMETRICS International Conference on Measurement and Modeling of Computer Systems (SIGMETRICS 2025)
Unicontainer: Unlocking the Potential of Unikernel for Secure and Efficient ContainerizationContainer VirtualizationACM SIGMETRICS International Conference on Measurement and Modeling of Computer Systems (SIGMETRICS 2025)Container technology, characterized by its convenience in deployment and exceptional performance, has emerged as a dominant force in the realm of cloud computing. However, the shared kernel among different containers and the common practice of running multiple applications within a single container pose threats to user data from malicious co-resident containers or other malicious programs within the same container. To address this problem, we introduce a novel container architecture design - UniContainer. UniContainer partitions original containers, allowing each component to run within an independent customized Unikernel, thereby enhancing isolation both between containers and within containers. We implement a prototype of UniContainer based on Unikraft, enabling automated analysis of target container system call logs and configuration of optimal Unikraft images, while preserving the convenience of container technology deployment. Through experimental evaluation, we validate the effectiveness and performance of UniContainer, maximizing the outstanding performance benefits of container technology.
@inproceedings{zhicong2025unicontainer, title = {Unicontainer: Unlocking the Potential of Unikernel for Secure and Efficient Containerization}, author = {Zhang, Zhicong and Zhou, Qihang and Xu, Shaowen and Jiang, Nan and Zhang, Weijuan and Jia, Xiaoqi}, booktitle = {Proceedings of the 2025 ACM SIGMETRICS/International Conference on Measurement and Modeling of Computer Systems}, year = {2025}, } -
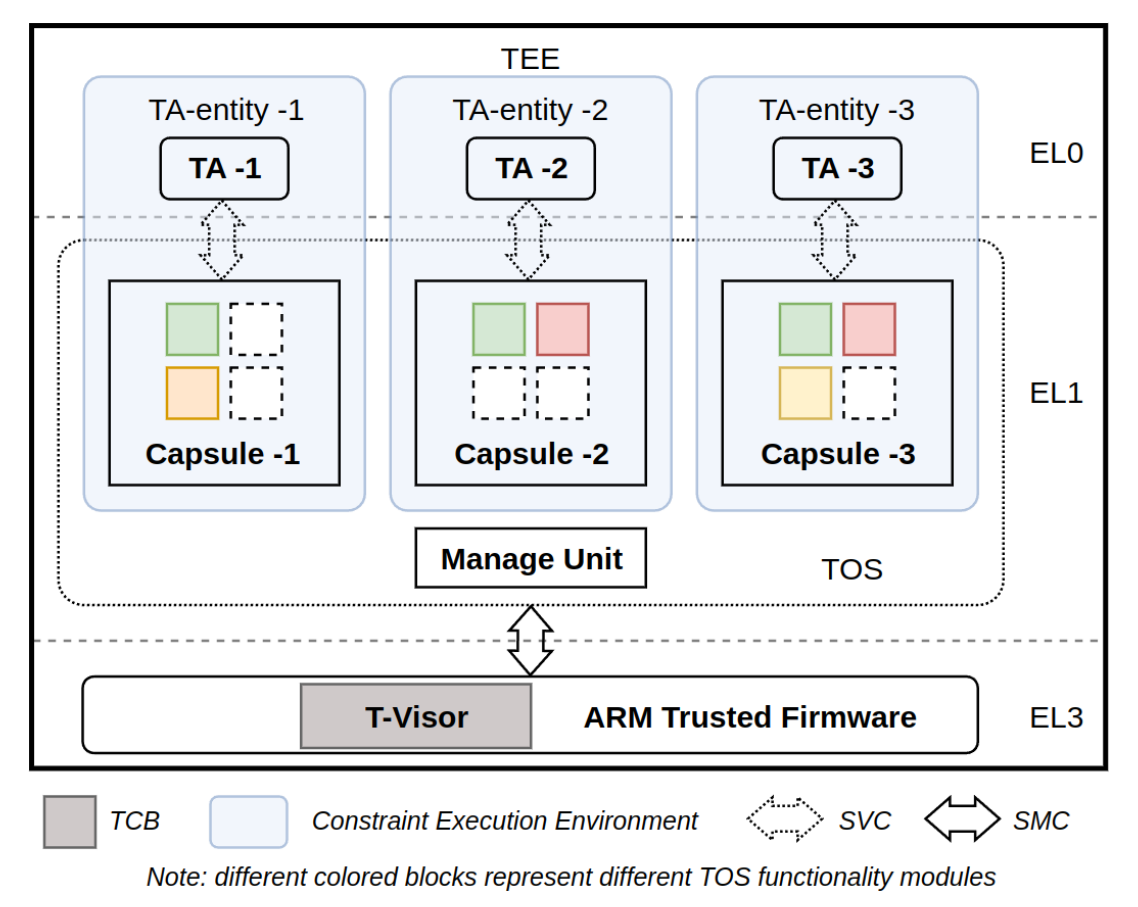 Chameleon: Towards Building Least-privileged TEE via Functionality-based Resource Re-groupingTEE MobileThe 23rd ACM International Conference on Mobile Systems, Applications, and Services (MobiSys 2025)
Chameleon: Towards Building Least-privileged TEE via Functionality-based Resource Re-groupingTEE MobileThe 23rd ACM International Conference on Mobile Systems, Applications, and Services (MobiSys 2025)TrustZone-assisted Trusted Execution Environment (TEE) has been widely employed in mobile devices to protect sensitive applications. With increased customization demands, Trusted Applications (TAs) have become more flexible and complex, exposing numerous vulnerabilities within the TEE. Furthermore, due to the unrestricted Trusted Operating System (TOS) services provided to TA, an attacker can exploit vulnerabilities to compromise the whole TEE system. In this paper, we propose a novel customized TOS partition approach, called Chameleon, to enhance the security of the TrustZone-assisted TEE system. Inspired by the principle of least privilege and our TEE vulnerability analysis, we first categorize the TOS into TOS service modules and basic kernel modules. Then, we selectively encapsulate these modules into distinct Capsules based on the TA’s functional requirements, providing each TA with a separate execution environment (TA-entity). To enforce access control and confine vulnerable modules within a TA-entity, we introduce T-Visor, which serves as our Trusted Computing Base. Our prototype implementation, built upon Linaro’s OP-TEE, requires only 2.9K Lines of Code (LoC) modifications. Evaluation on a Hikey960 board demonstrates that Chameleon reduces the attack surface of TOS services to 51% and mitigates 122 out of 138 CVEs (88.41%) with negligible performance overhead.
@inproceedings{nan2025chameleon, title = {Chameleon: Towards Building Least-privileged TEE via Functionality-based Resource Re-grouping}, author = {Jiang, Nan and Zhou, Qihang and Qian, Feifan and Chen, Jiayun and Huang, Heqing and Jia, Xiaoqi and Du, Haichao}, booktitle = {The 23rd ACM International Conference on Mobile Systems, Applications, and Services (MobiSys 2025)}, year = {2025}, } -
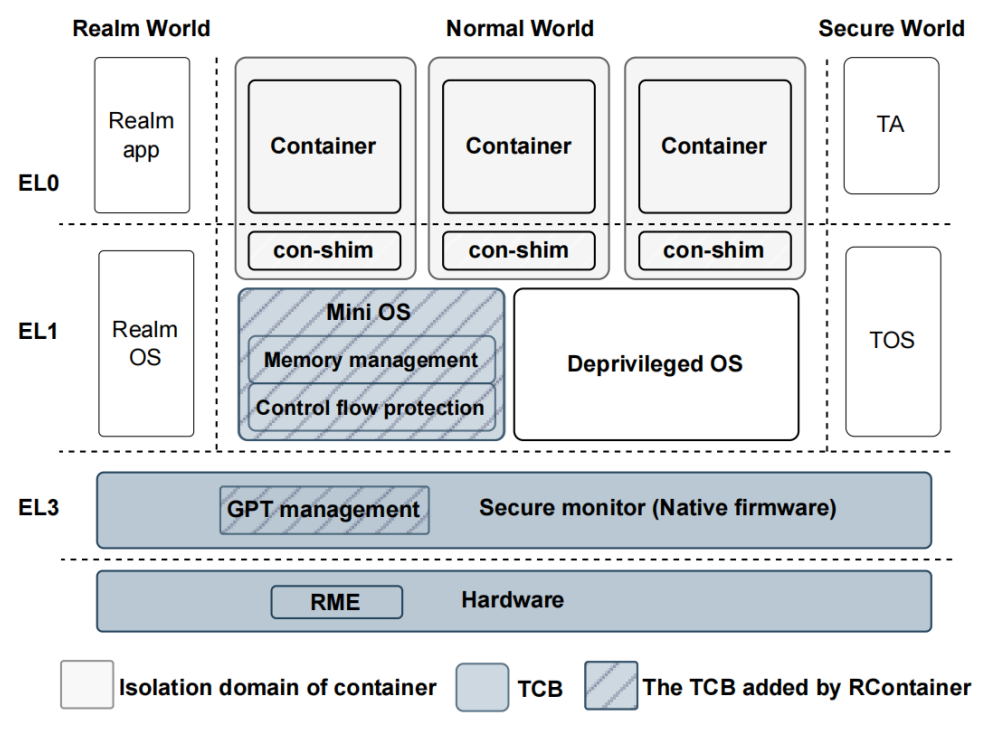 RContainer: A Secure Container Architecture through Extending ARM CCA Hardware PrimitivesTEE Container CCANetwork and Distributed System Security (NDSS) Symposium 2025
RContainer: A Secure Container Architecture through Extending ARM CCA Hardware PrimitivesTEE Container CCANetwork and Distributed System Security (NDSS) Symposium 2025Containers have become widely adopted in cloud platforms due to their efficient deployment and high resource utilization. However, their weak isolation has always posed a significant security concern. In this paper, we propose RContainer, a novel secure container architecture that protects containers from untrusted operating systems and enforces strong isolation among containers by extending ARM Confidential Computing Architecture (CCA) hardware primitives. RContainer introduces a small, trusted mini-OS that runs alongside the deprivileged OS, responsible for monitoring the control flow between the operating system and containers. Additionally, RContainer uses shim-style isolation, creating an isolated physical address space called con-shim for each container at the kernel layer through the Granule Protection Check mechanism. We have implemented RContainer on ARMv9-A Fixed Virtual Platform and ARMv8 hardware SoC for security analysis and performance evaluation. Experimental results demonstrate that RContainer can significantly enhance container security with a modest performance overhead and a minimal Trusted Computing Base (TCB).
@inproceedings{qihang2025rcontainer, title = {RContainer: A Secure Container Architecture through Extending ARM CCA Hardware Primitives}, author = {Zhou, Qihang and Cao, Wenzhuo and Jia, Xiaoqi and Liu, Peng and Zhang, Shengzhi and Chen, Jiayun and Xu, Shaowen and Song, Zhenyu}, booktitle = {Network and Distributed Systems Security Symposium (NDSS)}, year = {2025}, } -
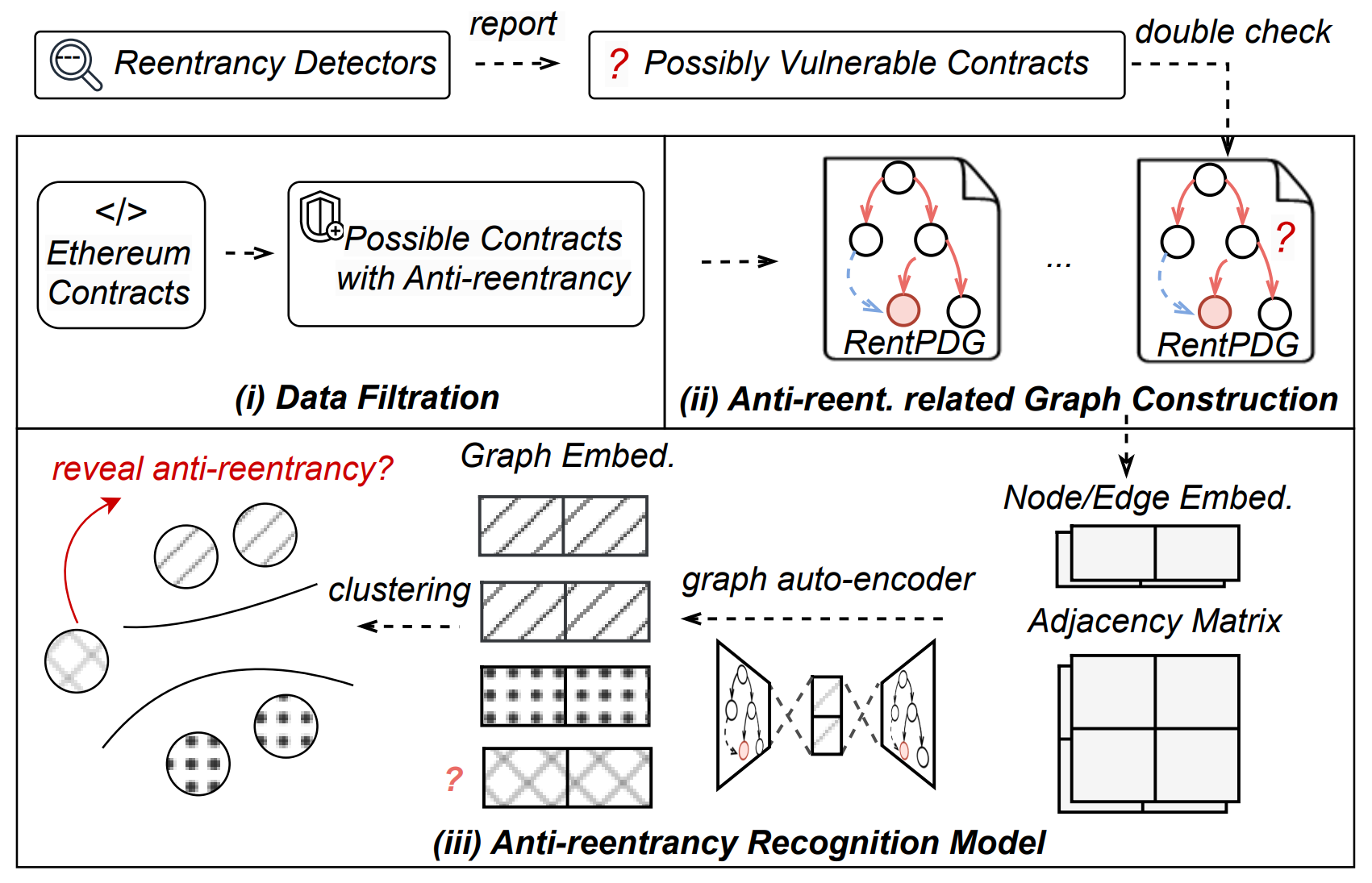 Silence False Alarms: Identifying Anti-Reentrancy Patterns on Ethereum to Refine Smart Contract Reentrancy DetectionAIQ. Song , H. Huang , X. Jia , Y. Xie , and J. CaoNetwork and Distributed System Security (NDSS) Symposium 2025
Silence False Alarms: Identifying Anti-Reentrancy Patterns on Ethereum to Refine Smart Contract Reentrancy DetectionAIQ. Song , H. Huang , X. Jia , Y. Xie , and J. CaoNetwork and Distributed System Security (NDSS) Symposium 2025Reentrancy vulnerabilities in Ethereum smart contracts have caused significant financial losses, prompting the creation of several automated reentrancy detectors. However, these detectors frequently yield a high rate of false positives due to coarse detection rules, often misclassifying contracts protected by anti-reentrancy patterns as vulnerable. Thus, there is a critical need for the development of specialized automated tools to assist these detectors in accurately identifying anti-reentrancy patterns. While existing code analysis techniques show promise for this specific task, they still face significant challenges in recognizing anti-reentrancy patterns. These challenges are primarily due to the complex and varied features of anti-reentrancy patterns, compounded by insufficient prior knowledge about these features. This paper introduces AutoAR, an automated recognition system designed to explore and identify prevalent anti-reentrancy patterns in Ethereum contracts. AutoAR utilizes a specialized graph representation, RentPDG, combined with a data filtration approach, to effectively capture anti-reentrancy-related semantics from a large pool of contracts. Based on RentPDGs extracted from these contracts, AutoAR employs a recognition model that integrates a graph auto-encoder with a clustering technique, specifically tailored for precise anti-reentrancy pattern identification. Experimental results show AutoAR can assist existing detectors in identifying 12 prevalent anti-reentrancy patterns with 89% accuracy, and when integrated into the detection workflow, it significantly reduces false positives by over 85%.
@inproceedings{qiyang2025autoar, title = {Silence False Alarms: Identifying Anti-Reentrancy Patterns on Ethereum to Refine Smart Contract Reentrancy Detection}, author = {Song, Qiyang and Huang, Heqing and Jia, Xiaoqi and Xie, Yuanbo and Cao, Jiahao}, booktitle = {Network and Distributed Systems Security Symposium (NDSS)}, year = {2025}, }
2024
-
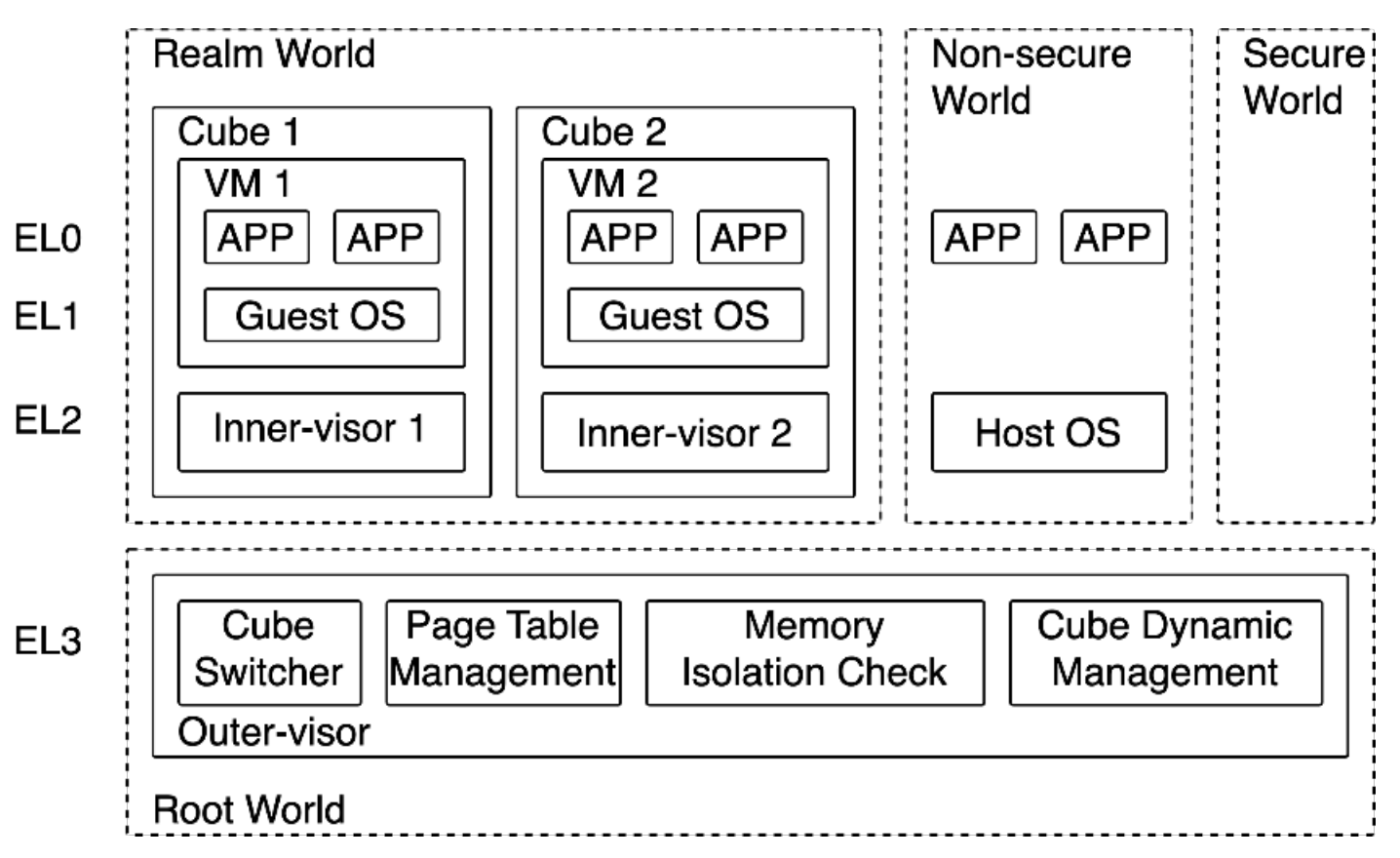 CubeVisor: A Multi-realm Architecture Design for Running VM with ARM CCATEE CCA VirtualizationProceedings of the 40th Annual Computer Security Applications Conference (ACSAC 2024)
CubeVisor: A Multi-realm Architecture Design for Running VM with ARM CCATEE CCA VirtualizationProceedings of the 40th Annual Computer Security Applications Conference (ACSAC 2024)Cloud computing nowadays provides flexible and scalable computing services, using different hardware platforms, including ARM. Virtualization allows multiple virtual machines (VMs) to share the physical resources of a host machine. However, these technologies have security risks. The hypervisor is the software that controls VMs, and it can be exploited or manipulated by hackers or untrusted providers. ARM CCA, a novel feature of ARMv9-A, allows confidential VMs to run in a new security state called realm. However, the current CCA prototype still has some problems, including risks brought by external libraries, single point of failure, highly privileged TF-RMM and costly world switch. In this paper, we introduce CubeVisor, a new secure virtualization architecture based on ARM CCA. It uses the idea of the Cube, which is a combination of a hypervisor and a VM, protecting each Cube from other Cubes or components. The CubeVisor also improves performance by optimizing memory allocation and world-switching processes. We implement prototypes on both software-based ARM FVP platform and hardware-based ARM Cortex-A platform for evaluations. The results show that the CubeVisor can protect VMs well and has very low overhead compared to the CCA based virtualization methods.
@inproceedings{jiayun2024cubevisor, title = {CubeVisor: A Multi-realm Architecture Design for Running VM with ARM CCA}, author = {Chen, Jiayun and Zhou, Qihang and Yan, Xiaolong and Jiang, Nan and Jia, Xiaoqi and Zhang, Weijuan}, booktitle = {2024 Annual Computer Security Applications Conference (ACSAC)}, pages = {1-13}, year = {2024}, doi = {10.1109/ACSAC63791.2024.00023}, } -
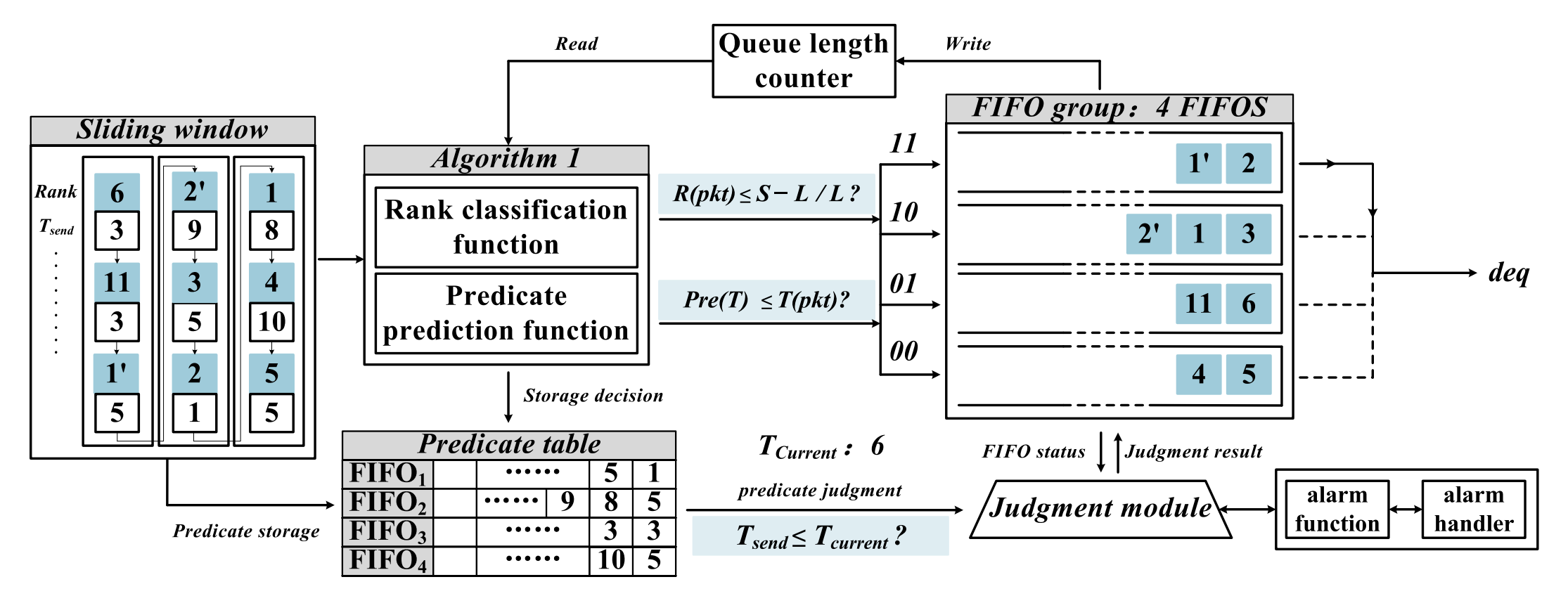 CIPO: Efficient, lightweight and programmable packet schedulingNetworkF. Guo , S. Sun , J. Hu , N. Zhang , and Z. LvComputer Networks, Volume 245, May 2024
CIPO: Efficient, lightweight and programmable packet schedulingNetworkF. Guo , S. Sun , J. Hu , N. Zhang , and Z. LvComputer Networks, Volume 245, May 2024With the rapid development of network devices and increasingly high CPU workloads, packet scheduling will have to be offloaded to hardware. Programmable packet scheduling allows scheduling algorithms to be programmed into network devices without modifying the hardware. It not only retains the flexibility of software but also the scalability of hardware. In existing primitives, the most expressive Push-In-ExtractOut (PIEO) is prohibitively expensive to implement due to its complexity. While its variant, Push-In-Pick-Out (PIPO), offers some improvements, it suffers from insufficient scalability. In this paper, we propose the Classify-In-Push-Out (CIPO) primitive. The core idea of CIPO is to track the rank and predicate of recent packets through a sliding window, filter and classify packets using a prediction-based two-dimensional classification algorithm and a finite number of First-In-First-Out (FIFO) queues. Through theoretical analysis and evaluation with a range of real workloads, CIPO proves that it has a scheduling performance similar to the most expressive scheduling primitive. Importantly, CIPO requires fewer hardware resources while still providing sufficient expressiveness. Primitive on FPGA show that the CIPO-based scheduler achieves an average of 1.24x higher throughput than the PIEO-based scheduler but uses only an average of 26.2% of look-up tables (LUTs) and 12.2% of the block RAM of the latter.
@article{feng2024computernetworks, title = {CIPO: Efficient, lightweight and programmable packet scheduling}, author = {Guo, Feng and Sun, Shidong and Hu, Junjie and Zhang, Ning and Lv, Zhiqiang}, year = {2024}, journal = {Computer Networks}, volume = {245}, pages = {110355}, issn = {1389-1286}, doi = {10.1016/j.comnet.2024.110355}, } -
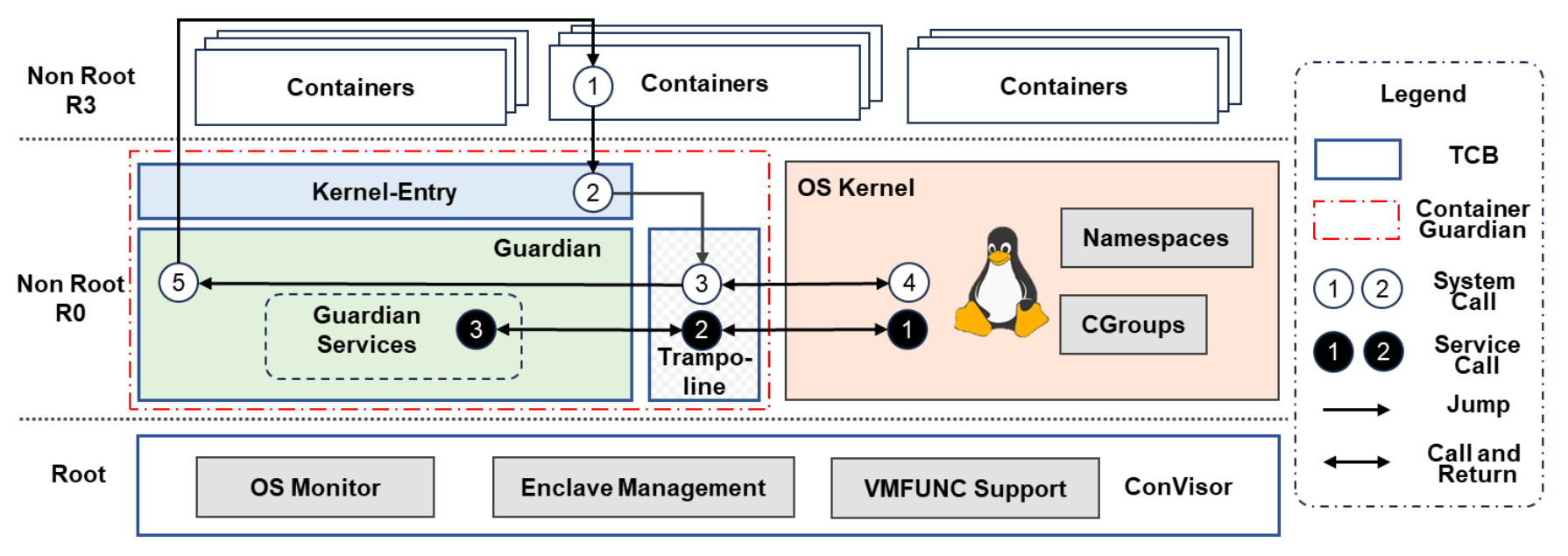 ConMonitor: Lightweight Container Protection with Virtualization and VM FunctionsContainer VirtualizationProceedings of the 2024 ACM Symposium on Cloud Computing (SoCC ’24)
ConMonitor: Lightweight Container Protection with Virtualization and VM FunctionsContainer VirtualizationProceedings of the 2024 ACM Symposium on Cloud Computing (SoCC ’24)Containers are widely used in multi-tenant cloud computing for their ease of deployment, minimal overhead, and fast start-up. However, the intrinsic shared kernel model of containers poses significant security threats, risking confidentiality and integrity from co-located containers or compromised OS. Researchers have proposed various methods to protect containers from untrusted OS, but few consider both the universality and efficiency. In this paper, we present ConMonitor—a lightweight and efficient container protection architecture. ConMonitor protects the security of container application data by introducing a compact virtualization software, called ConVisor, as a trusted computing base. ConVisor enforces isolation of the physical memory between containers and the kernel, and monitors the sensitive operations performed by the OS. To ensure the security of ConMonitor, we implement a Container Guardian to serve as an intermediary for the kernel, managing sensitive operations. Moreover, we also leverage the VMFUNC feature to achieve fast context switching, thereby mitigating the performance penalty associated with frequent context switching. We have implemented ConMonitor on Intel CPU with Virtualization Technology, and the evaluation results show that ConMonitor can protect the security of container applications with a negligible performance overhead.
@inproceedings{shaowen2024conmonitor, title = {ConMonitor: Lightweight Container Protection with Virtualization and VM Functions}, author = {Xu, Shaowen and Zhou, Qihang and Zhang, Zhicong and Jia, Xiaoqi and Liu, Donglin and Huang, Heqing and Du, Haichao and Song, Zhenyu}, year = {2024}, isbn = {9798400712869}, publisher = {Association for Computing Machinery}, booktitle = {Proceedings of the 2024 ACM Symposium on Cloud Computing}, pages = {755-773}, doi = {10.1145/3698038.3698520}, } -
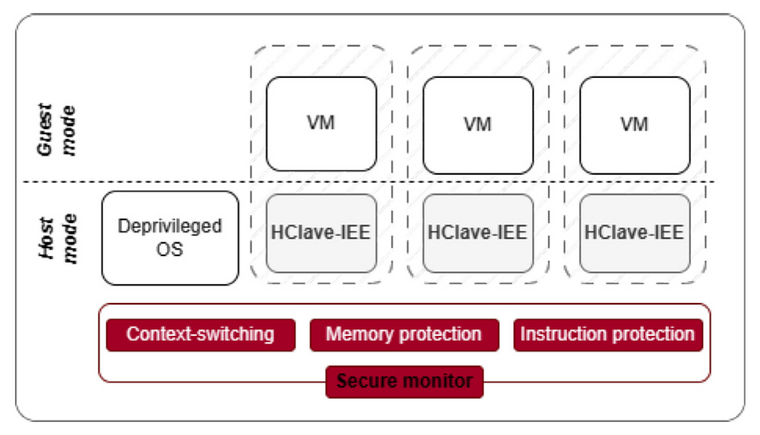 HClave: An isolated execution environment design for hypervisor runtime securityVirtualizationQ. Zhou , W. Cao , X. Jia , S. Zhang , J. Chen , N. Jiang , W. Zhang , H. Du , Z. Song , and Q. HuangComputers & Security, Volume 144, 2024
HClave: An isolated execution environment design for hypervisor runtime securityVirtualizationQ. Zhou , W. Cao , X. Jia , S. Zhang , J. Chen , N. Jiang , W. Zhang , H. Du , Z. Song , and Q. HuangComputers & Security, Volume 144, 2024Virtualization is the cornerstone of cloud computing, but the hypervisor, the crucial software component that enables virtualization, is known to suffer from various attacks. It is challenging to secure the hypervisor due to at least two reasons. On one hand, commercial hypervisors are usually integrated into a privileged Operating System (OS), which brings in a larger attack surface. On the other hand, multiple Virtual Machines (VM) share a single hypervisor, thus a malicious VM could leverage the hypervisor as a bridge to launch “cross-VM” attacks. In this work, we propose HClave, an isolated execution environment (IEE) design for hypervisor runtime. We decouple the virtualization layer into a tiny trusted computing base (TCB), a large non-secure OS, and multiple HClave IEEs through a bidirectional isolation approach. HClave extends the nested kernel approach to deprive the traditional OS from accessing the tiny TCB’s memory and creates an IEE for hypervisor runtime. We implemented HClave based on KVM and evaluated its effectiveness and efficiency through case studies. Experimental results show that HClave can significantly improve the security of the hypervisor with reasonable runtime overhead.
@article{qihang2024hclave, title = {HClave: An isolated execution environment design for hypervisor runtime security}, author = {Zhou, Qihang and Cao, Wenzhuo and Jia, Xiaoqi and Zhang, Shengzhi and Chen, Jiayun and Jiang, Nan and Zhang, Weijuan and Du, Haichao and Song, Zhenyu and Huang, Qingjia}, publisher = {Elsevier Advanced Technology Publications}, volume = {144}, number = {C}, issn = {0167-4048}, journal = {Comput. Secur.}, year = {2024}, doi = {10.1016/j.cose.2024.103923}, } -
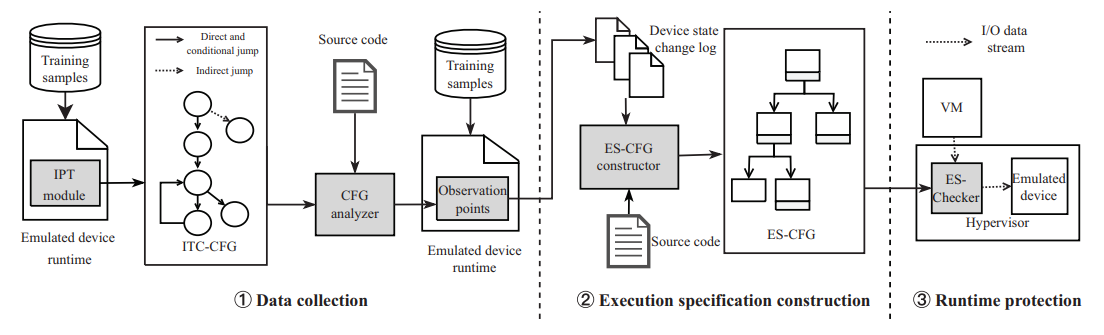 SEDSpec: Securing Emulated Devices by Enforcing Execution SpecificationVirtualizationThe 54th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN 2024)
SEDSpec: Securing Emulated Devices by Enforcing Execution SpecificationVirtualizationThe 54th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN 2024)Device emulation is a vital aspect of virtualization, yet remains vulnerable to security threats. Prior research has focused on monitoring I/O data flow or identifying internal device anomalies but often falls short in precision and automation. In this paper, we propose a novel method that leverages the normal operations of an emulated device to formulate an execution specification. The specification acts as a criterion to evaluate the device’s behavior and state transitions. We implement SEDSpec, a prototype system that automatically generates the execution specification for an emulated device and devises three check strategies for identifying any deviations from this specification, thereby ensuring normal operations and enhancing the security of the emulated device. We evaluate SEDSpec with five different execution specifications. The results show that SEDSpec can detect anomalies caused by vulnerability exploitation while maintaining the devices’ regular functioning with minimal performance overhead.
@inproceedings{yang2024sedspec, title = {SEDSpec: Securing Emulated Devices by Enforcing Execution Specification}, author = {Chen, Yang and Zhang, Shengzhi and Xiaoqi, Jia and Zhou, Qihang and Huang, Heqing and Xu, Shaowen and Du, Haichao}, booktitle = {2024 54th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN)}, pages = {522-534}, year = {2024}, doi = {10.1109/DSN58291.2024.00056}, } -
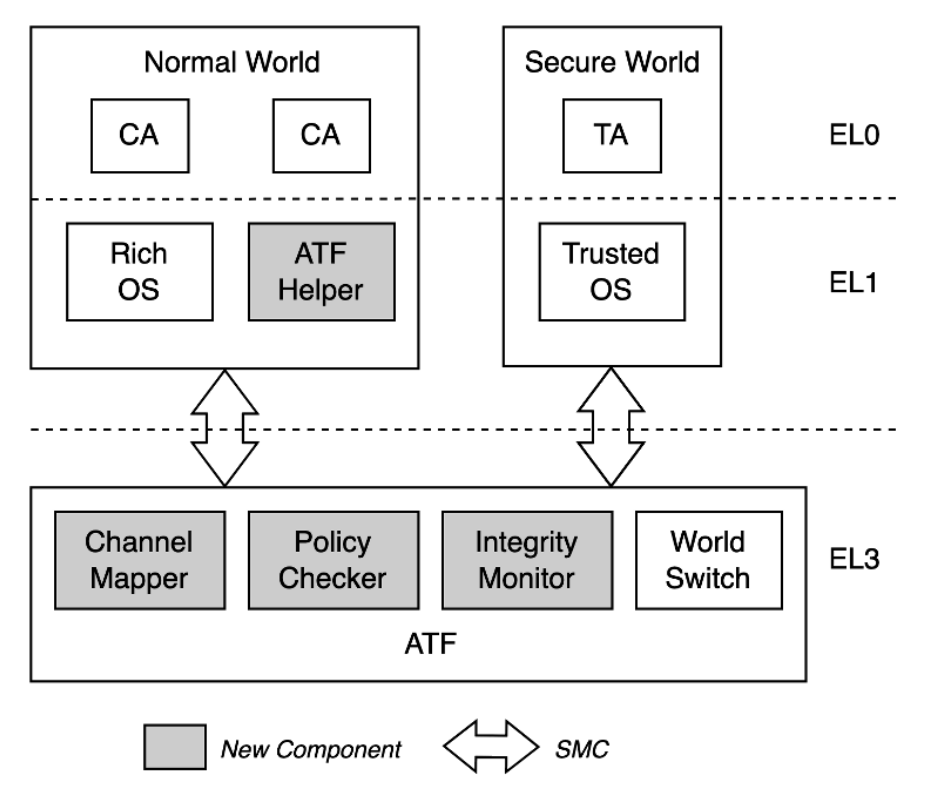 SeChannel: A Secure and Lightweight Channel Protection Approach for TEE SystemsTEE23rd International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom 2024)
SeChannel: A Secure and Lightweight Channel Protection Approach for TEE SystemsTEE23rd International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom 2024)Trusted Execution Environments (TEEs) are essential for securing sensitive data by isolating it from potentially vulnerable execution environments. In ARM-based devices, TEEs utilize TrustZone technology to create a secure world for Trusted Applications (TAs) and a normal world for Client Applications (CAs), ensuring strict isolation through hardware mechanisms. Despite this protection, current TEE systems lack robust mechanisms for securing TA access, leaving them vulnerable to attacks that exploit cross-world communication channels.This paper introduces SeChannel, a lightweight solution for securing communication channels in TrustZone-assisted TEEs. Unlike existing methods, SeChannel requires no additional hardware and avoids the performance penalties of encryption and memory copying. By leveraging existing ARM Trusted Firmware (ATF), SeChannel implements fine-grained access control to ensure that communication between CAs and TAs is authenticated and protected. It verifies shared memory addresses and TA sessions, preventing unauthorized access by the Rich OS. We implement a prototype of SeChannel on the Hikey960 development board with minimal code modifications to the existing system. Our evaluation demonstrates that SeChannel significantly enhances the security of TrustZone-assisted TEEs with negligible performance overhead.
@inproceedings{nan2024sechannel, title = {SeChannel: A Secure and Lightweight Channel Protection Approach for TEE Systems}, author = {Jiang, Nan and Zhao, Yuanbo and Zhou, Qihang and Jia, Xiaoqi and Tang, Jing}, booktitle = {2024 IEEE 23rd International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom)}, pages = {77-84}, year = {2024}, doi = {10.1109/TrustCom63139.2024.00038}, } -
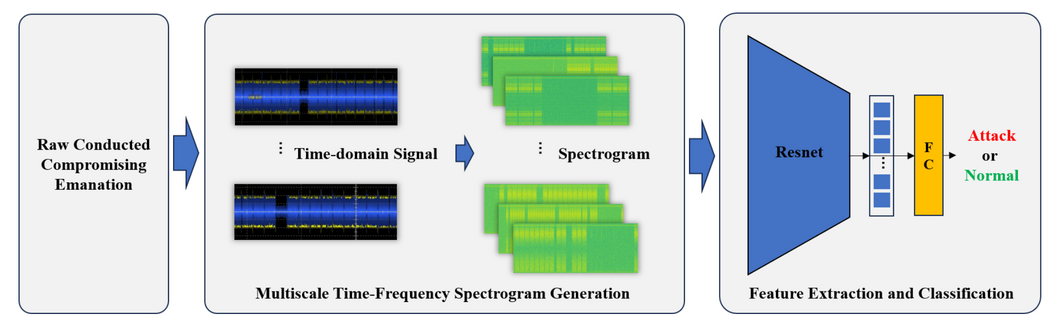 USB Catcher: Detection of Controlled Emissions via Conducted Compromising EmanationsUSBY. Zhang , F. Du , X. Chi , and Z. Lv23rd International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom 2024)
USB Catcher: Detection of Controlled Emissions via Conducted Compromising EmanationsUSBY. Zhang , F. Du , X. Chi , and Z. Lv23rd International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom 2024)The security of the Universal Serial Bus (USB) is critical due to its widespread use. Attackers can exploit electromagnetic emissions from USB devices to steal sensitive information, and detecting controlled emissions from USB has long been a challenging issue. Existing methods for detecting controlled emissions based on radiated compromising emanations are often hindered by environmental noise, electromagnetic interference, and device variability, leading to reduced detection capability. To address these challenges, this paper, for the first time, proposes a method for detecting controlled emissions from USB devices through conducted compromising emanations. First, we construct a dataset of USB leakage signals based on conducted compromising emanations. Then, we propose a multiscale time-frequency processing technique for USB leakage signals, applying time-frequency analysis to generate spectrograms containing both time-domain and frequency-domain features. By leveraging multiscale data augmentation, the accuracy and generalization of detection model are enhanced. Finally, we employ a Residual Network to automatically extract features and detect abnormal signals. Extensive experiments demonstrate that this method can effectively identify controlled emissions from USB devices, achieving an AUC of 99.52% and an ACC of 96.74%, providing a robust solution for anomaly detection and enhancing the security of USB devices.
@inproceedings{yixin2024usbcatcher, title = {USB Catcher: Detection of Controlled Emissions via Conducted Compromising Emanations}, author = {Zhang, Yixin and Du, Fuqiang and Chi, Xinge and Lv, Zhiqiang}, booktitle = {2024 IEEE 23rd International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom)}, pages = {1296-1303}, year = {2024}, doi = {10.1109/TrustCom63139.2024.00182}, } -
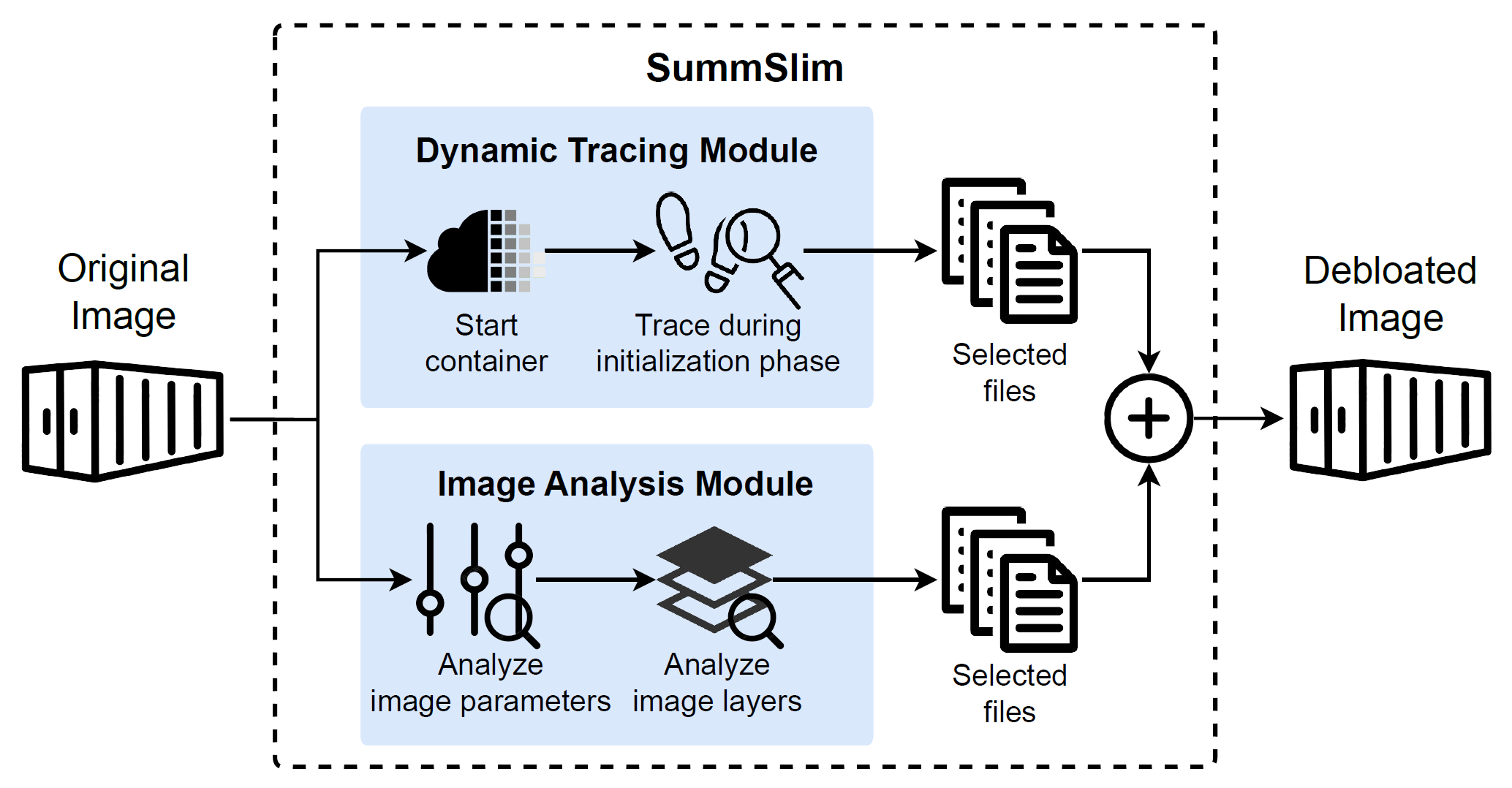 SummSlim: A Universal and Automated Approach for Debloating Container ImagesContainer30th International Conference on Parallel and Distributed Systems (ICPADS 2024)
SummSlim: A Universal and Automated Approach for Debloating Container ImagesContainer30th International Conference on Parallel and Distributed Systems (ICPADS 2024)Container technology has become a cornerstone of cloud computing, offering notable benefits such as enhanced resource utilization and streamlined deployment processes. The adoption of container technology by leading cloud service providers has steadily increased over the years. However, during the image construction phase, the reuse of base images and the execution of certain commands often results in the retention of redundant files, leading to resource wastage and potential security vulnerabilities. In this research, we systematically review and analyze existing methodologies, identify shortcomings in current approaches, and propose an automated image debloating tool named SummSlim according to the characteristics of the container image construction process. We selected 195 official images from Docker Hub for testing and evaluated the effectiveness of SummSlim with a success rate of 98.46%. Then we compare and analyze the images before and after debloating, and make some novel suggestions for developers. To the best of our knowledge, SummSlim is the first practically available universal image debloating tool.
@inproceedings{zhicong2024summslim, title = {SummSlim: A Universal and Automated Approach for Debloating Container Images}, author = {Zhang, Zhicong and Huang, Heqing and Xu, Shaowen and Zhou, Qihang and Zhang, Tianshu and Jia, Xiaoqi and Zhang, Weijuan}, booktitle = {2024 IEEE 30th International Conference on Parallel and Distributed Systems (ICPADS)}, pages = {132-141}, publisher = {IEEE Computer Society}, year = {2024}, doi = {10.1109/ICPADS63350.2024.00027}, } -
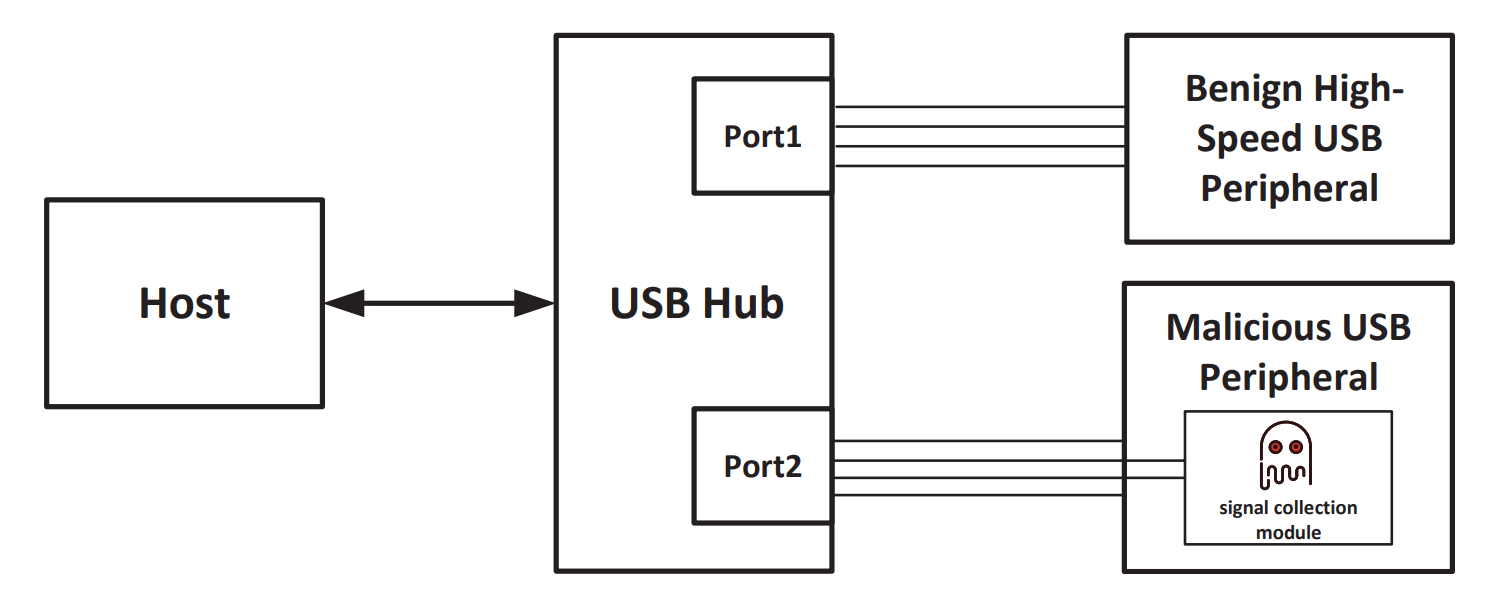 A Conducted Compromising Emanations Method on High-Speed USB Devices via USB HubsUSBY. Zhang , H. Li , Q. Ye , J. Hu , Y. Han , and Z. Lv2024 IEEE Symposium on Computers and Communications (ISCC)
A Conducted Compromising Emanations Method on High-Speed USB Devices via USB HubsUSBY. Zhang , H. Li , Q. Ye , J. Hu , Y. Han , and Z. Lv2024 IEEE Symposium on Computers and Communications (ISCC)High-speed USB is prominently used in electronic devices, such as computers and mass storage devices, where sensitive data may be stored. There are risks of information leakage by conducted compromising emanations during data transmission with high-speed USB devices. Therefore, it is of great significance to research and analyze the security issues of high-speed USB for maintaining information security. However, little research is done on conducted compromising emanations of high-speed USB. In this paper, we propose a method to attack high-speed USB devices by conducted compromising emanations through USB hubs. First, we construct a USB hub-based attack model for high-speed USB devices. Then, we design a filtering mechanism with Kaiser filter to preprocess the collected leakage signal to obtain a cleaner leakage signal. Finally, by decoding and reconstructing the processed signal, the attack on the high-speed USB device is realized. Extensive experiments show that the method proposed in this paper can successfully attack high-speed USB devices, achieving a Bit-level Accuracy of 99.69% and a Character-level Accuracy of 98.04%. This demonstrates that our attack method is effective and verifies the existence of information leakage risk from high-speed USB devices through conducted compromising emanations in USB Hubs.
@inproceedings{yixin2024highspeedusbattack, title = {A Conducted Compromising Emanations Method on High-Speed USB Devices via USB Hubs}, author = {Zhang, Yixin and Li, Haiyang and Ye, Qingqing and Hu, Junjie and Han, Yinglong and Lv, Zhiqiang}, booktitle = {2024 IEEE Symposium on Computers and Communications (ISCC)}, pages = {1-8}, year = {2024}, doi = {10.1109/ISCC61673.2024.10733582}, } -
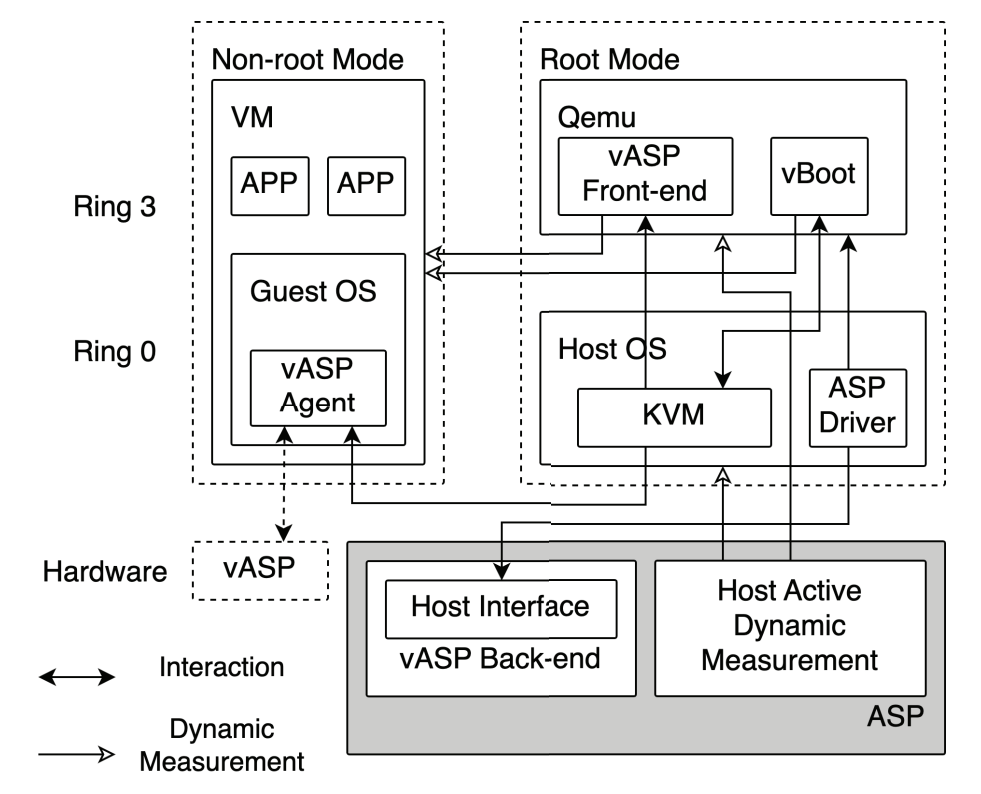 vASP: Full VM Life-cycle Protection Based on Active Security Processor ArchitectureVirtualization24th International Symposium on Cluster, Cloud and Internet Computing (CCGrid 2024)
vASP: Full VM Life-cycle Protection Based on Active Security Processor ArchitectureVirtualization24th International Symposium on Cluster, Cloud and Internet Computing (CCGrid 2024)Cloud computing has been applied on a large scale due to its competitive advantages. However, the introduction of virtualization brings new risks, which can come from within the VM and the host. Due to the abstraction of hardware resources by the hypervisor, traditional trusted computing methods, such as TPM and ASP, are no longer available in cloud environments. Existing work focusing on enabling trusted computing in cloud computing is primarily based on TPM and vTPM, but there are still issues such as the trusted chain not covering all stages of the VM life cycle and the integrity measurement operation potentially causing high overhead. In this paper, we present the vASP architecture, which solves the limitation of the ASP architecture in a cloud environment. Using customization features provided by the ASP, we customize interfaces for the vASP architecture and pass the trusted relationship to the upper layer to form a complete chain of trust. The vASP front-end plugs into the hypervisor actively and regularly operates the dynamic measurement process of the guest to ensure that data from the guest machine are not tampered with. With the introduction of vASP in the cloud computing platform, the security of vASP components during VM operation is also a concern. As a result, we propose a full VM life-cycle protection method through verification and measurement mechanisms that cannot be bypassed to ensure that vASP maintains a match with specific VMs. We have implemented the vASP architecture on a commercial platform deployed with ASP architecture and evaluated it. The result shows that the vASP architecture can protect VM integrity well during full life-cycle and has very low overhead compared to the native virtualization architecture.
@inproceedings{jiayun2024vasp, title = {vASP: Full VM Life-cycle Protection Based on Active Security Processor Architecture}, author = {Chen, Jiayun and Zhou, Qihang and Zhang, Weijuan and Jiang, Nan and Xie, Yamin and Jia, Xiaoqi}, booktitle = {2024 IEEE 24th International Symposium on Cluster, Cloud and Internet Computing (CCGrid)}, pages = {168-177}, year = {2024}, doi = {10.1109/CCGrid59990.2024.00028}, } -
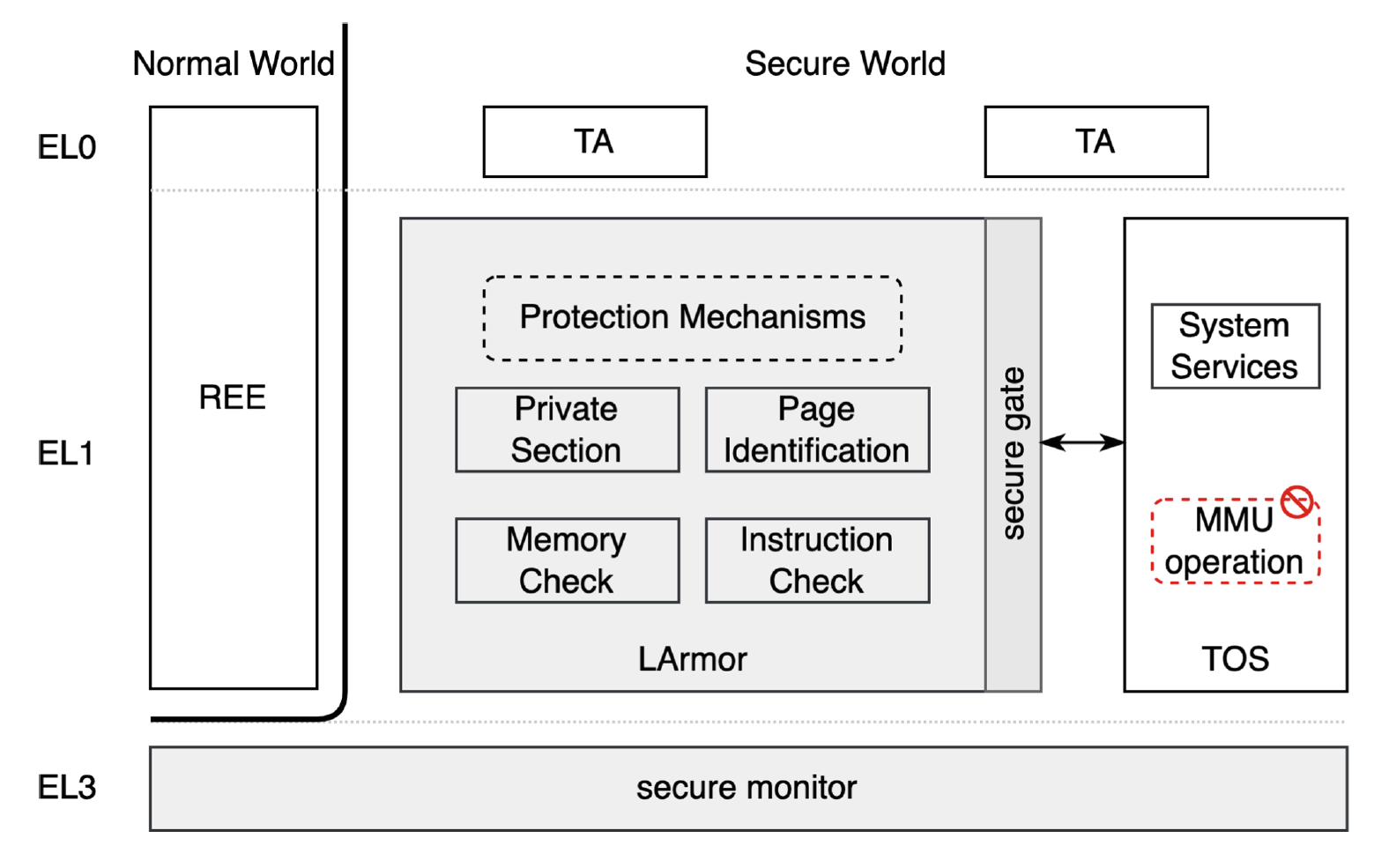 LightArmor: A Lightweight Trusted Operating System Isolation Approach for Mobile SystemsTEE Mobile39th IFIP International Information Security Conference (IFIPSEC 2024)
LightArmor: A Lightweight Trusted Operating System Isolation Approach for Mobile SystemsTEE Mobile39th IFIP International Information Security Conference (IFIPSEC 2024)Mobile systems extensively leverage Trusted Execution Environments (TEEs) to protect sensitive applications. However, the Trusted Operating System (TOS), as a critical component of TEE, has exposed many vulnerabilities in recent years. With the high privilege of TOS, an attacker who gains control of TOS can take over arbitrary system components, and the privacy of the system can no longer be guaranteed. Although existing methods provide multiple dependent environments to confine the impact into a single TOS instance, they cause substantial memory duplicates of TOS within the resource-constrained TEE. This paper proposes a lightweight isolation approach called LightArmor for TEE-based mobile systems. LightArmor provides protection mechanisms in a tiny context (LArmor) that guarantees the security of other components even if TOS is compromised. Specifically, LightArmor deprives TOS of memory management privilege and provides protection mechanisms to limit TOS’s ability to perform privileged operations. To guarantee the security of LArmor, we feature a non-bypassable memory isolation mechanism through virtualizing memory management unit. We evaluate LightArmor in a real-world Hikey960 development board. Experimental results demonstrate that LightArmor can enhance system security with a negligible performance overhead.
@inproceedings{nan2024lightarmor, title = {LightArmor: A Lightweight Trusted Operating System Isolation Approach for Mobile Systems}, author = {Jiang, Nan and Zhou, Qihang and Jia, Xiaoqi and Chen, Jiayun and Huang, Qingjia and Du, Haichao}, booktitle = {ICT Systems Security and Privacy Protection}, pages = {206--220}, isbn = {978-3-031-65175-5}, year = {2024}, publisher = {Springer Nature Switzerland}, doi = {10.1007/978-3-031-65175-5_15}, }
2023
-
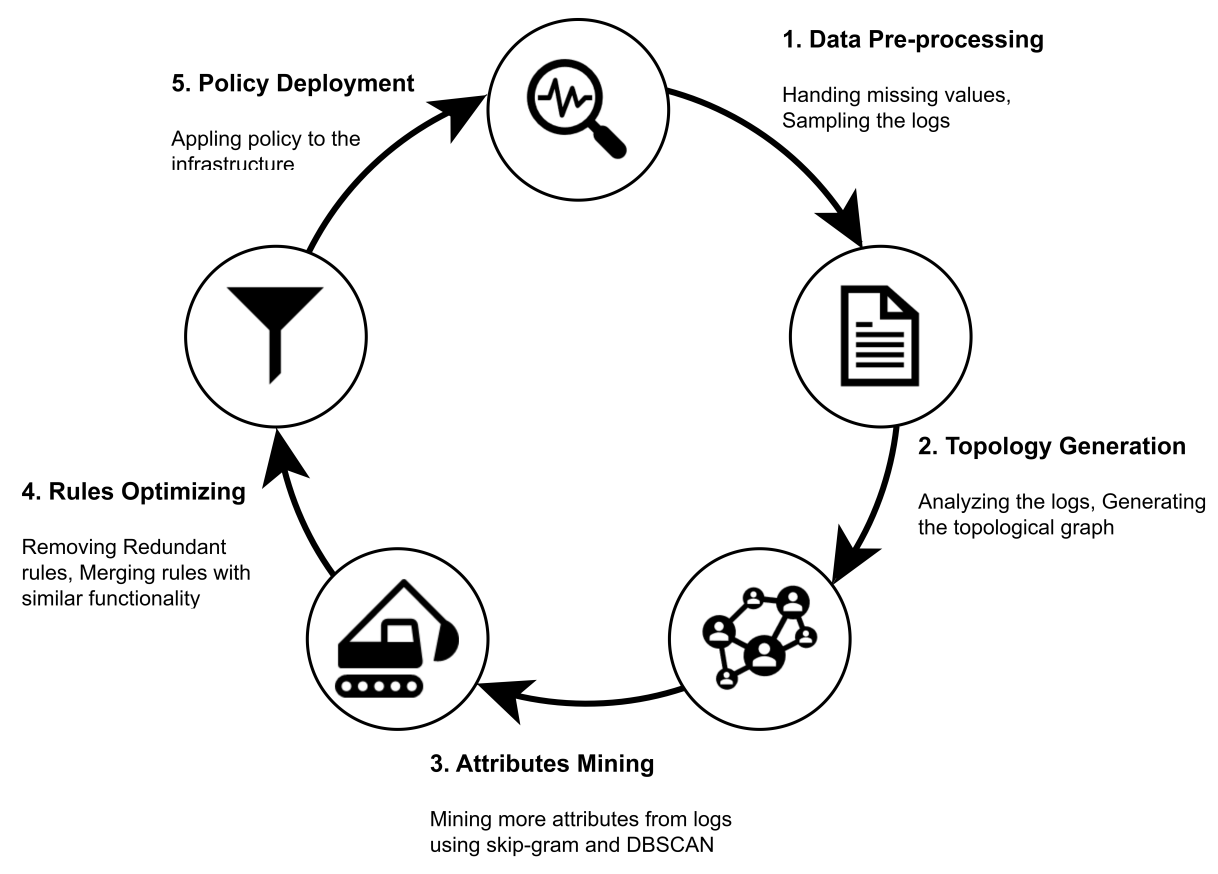 Log2Policy: An Approach to Generate Fine-Grained Access Control Rules for Microservices from ScratchAI CloudProceedings of the 39th Annual Computer Security Applications Conference (ACSAC 2023)
Log2Policy: An Approach to Generate Fine-Grained Access Control Rules for Microservices from ScratchAI CloudProceedings of the 39th Annual Computer Security Applications Conference (ACSAC 2023)Microservice application architecture is one of the most widely used service architectures in the industry. To prevent a compromised microservice from abusing other microservices, authorization policy is applied to regulate the access among them. However, configuring access control policy manually is challenging due to the complexity and dynamic nature of microservice applications. In this paper, we present Log2Policy, a novel approach to generate microservice authorization policy based on access logs. Our approach consists of three fundamental techniques: (1) a log-based topological graph generation mechanism that automatically infers the invocation logic among microservices, (2) a machine learning based attributes mining method that extracts the relevant attributes of requests, and (3) a policy upgrade mechanism based on traffic management that can significantly reduce the upgrade time. We have implemented a prototype of Log2Policy on mainstream microservice infrastructures and have evaluated it with several microservice applications. The results show that Log2Policy can generate fine-grained and effective access control rules and upgrade them with negligible overhead.
@inproceedings{shaowen2023log2policy, title = {Log2Policy: An Approach to Generate Fine-Grained Access Control Rules for Microservices from Scratch}, author = {Xu, Shaowen and Zhou, Qihang and Huang, Heqing and Jia, Xiaoqi and Du, Haichao and Chen, Yang and Xie, Yamin}, year = {2023}, isbn = {9798400708862}, publisher = {Association for Computing Machinery}, booktitle = {Proceedings of the 39th Annual Computer Security Applications Conference}, pages = {229-240}, doi = {10.1145/3627106.3627137}, }
2022
-
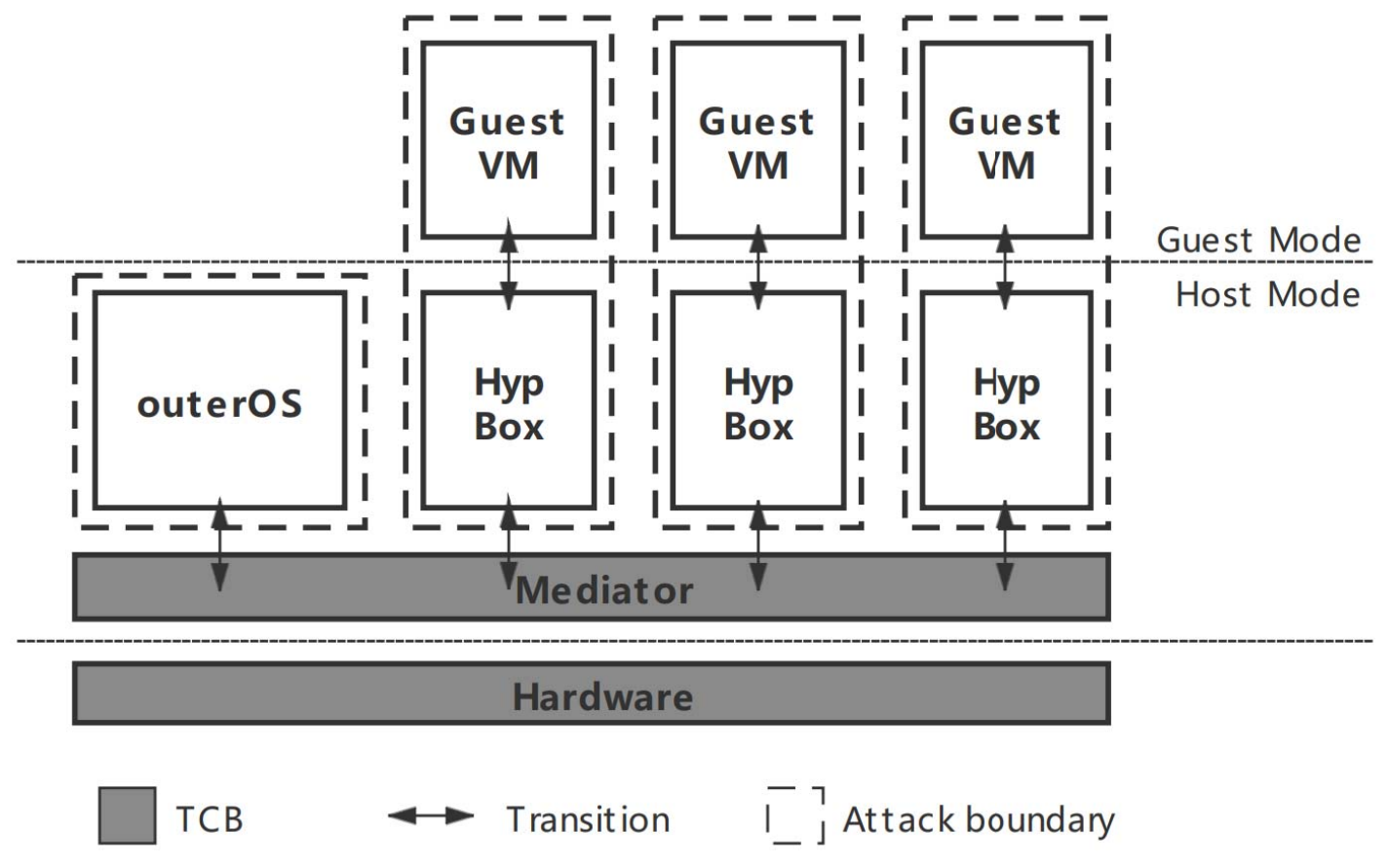 SecFortress: Securing Hypervisor using Cross-layer IsolationVirtualization39th IEEE International Parallel & Distributed Processing Symposium (IPDPS 2022)
SecFortress: Securing Hypervisor using Cross-layer IsolationVirtualization39th IEEE International Parallel & Distributed Processing Symposium (IPDPS 2022)Virtualization is the corner stone of cloud computing, but the hypervisor, the crucial software component that enables virtualization, is known to suffer from various attacks. It is challenging to secure the hypervisor due to at least two reasons. On one hand, commercial hypervisors are usually integrated into a privileged Operating System (OS), which brings in a larger attack surface. On the other hand, multiple Virtual Machines (VM) share a single hypervisor, thus a malicious VM could leverage the hypervisor as a bridge to launch “cross-VM” attacks. In this work, we propose SecFortress, a dependable hypervisor design that decouples the virtualization layer into a mediator, an outerOS, and multiple HypBoxes through a cross-layer isolation approach. SecFortress extends the nested kernel approach to de-privilege the outerOS from accessing the mediator’s memory and creates an isolated hypervisor instance, HypBox, to confine the impacts from the untrusted VMs. We implemented SecFortress based on KVM and evaluated its effectiveness and efficiency through case studies and performance evaluation. Experimental results show that SecFortress can significantly improve the security of the hypervisor with negligible runtime overhead.
@inproceedings{qihang2022secfortress, title = {SecFortress: Securing Hypervisor using Cross-layer Isolation}, author = {Zhou, Qihang and Jia, Xiaoqi and Zhang, Shengzhi and Jiang, Nan and Chen, Jiayun and Zhang, Weijuan}, booktitle = {2022 IEEE International Parallel and Distributed Processing Symposium (IPDPS)}, pages = {212-222}, year = {2022}, doi = {10.1109/IPDPS53621.2022.00029}, }
2020
-
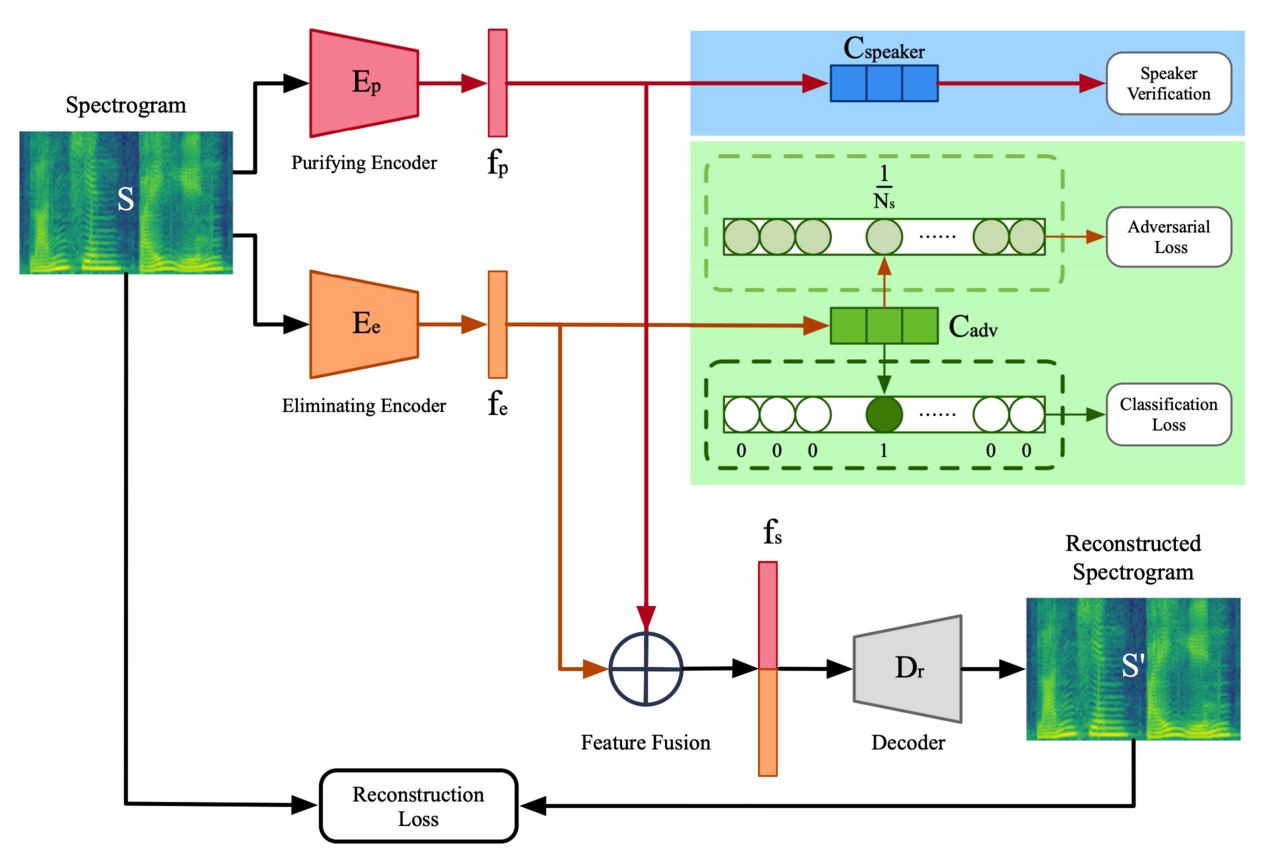 SEEF-ALDR: A Speaker Embedding Enhancement Framework via Adversarial Learning based Disentangled RepresentationAIProceedings of the 36th Annual Computer Security Applications Conference
SEEF-ALDR: A Speaker Embedding Enhancement Framework via Adversarial Learning based Disentangled RepresentationAIProceedings of the 36th Annual Computer Security Applications ConferenceSpeaker verification, as a biometric authentication mechanism, has been widely used due to the pervasiveness of voice control on smart devices. However, the task of “in-the-wild” speaker verification is still challenging, considering the speech samples may contain lots of identity-unrelated information, e.g., background noise, reverberation, emotion, etc. Previous works focus on optimizing the model to improve verification accuracy, without taking into account the elimination of the impact from the identity-unrelated information. To solve the above problem, we propose SEEF-ALDR, a novel Speaker Embedding Enhancement Framework via Adversarial Learning based Disentangled Representation, to reinforce the performance of existing models on speaker verification. The key idea is to retrieve as much speaker identity information as possible from the original speech, thus minimizing the impact of identity-unrelated information on the speaker verification task by using adversarial learning. Experimental results demonstrate that the proposed framework can significantly improve the performance of speaker verification by 20.3% and 23.8% on average over 13 tested baselines on dataset Voxceleb1 and 8 tested baselines on dataset Voxceleb2 respectively, without adjusting the structure or hyper-parameters of them. Furthermore, the ablation study was conducted to evaluate the contribution of each module in SEEF-ALDR. Finally, porting an existing model into the proposed framework is straightforward and cost-efficient, with very little effort from the model owners due to the modular design of the framework.
@inproceedings{jianwei2020seef-aldr, title = {SEEF-ALDR: A Speaker Embedding Enhancement Framework via Adversarial Learning based Disentangled Representation}, author = {Tai, Jianwei and Jia, Xiaoqi and Huang, Qingjia and Zhang, Weijuan and Du, Haichao and Zhang, Shengzhi}, booktitle = {Proceedings of the 36th Annual Computer Security Applications Conference}, pages = {939-950}, year = {2020}, isbn = {9781450388580}, publisher = {Association for Computing Machinery}, doi = {10.1145/3427228.3427274}, } -
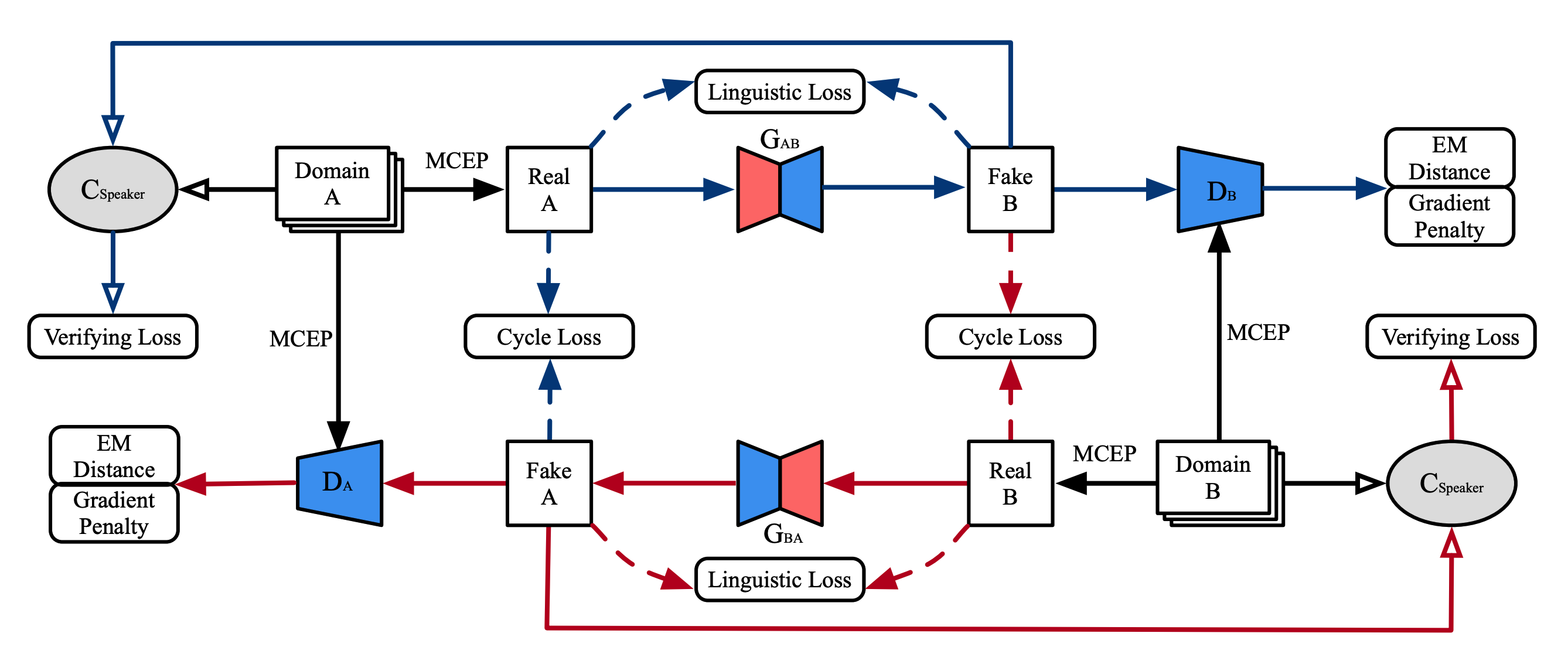 ET-GAN: Cross-Language Emotion Transfer Based on Cycle-Consistent Generative Adversarial NetworksAIThe 24th European Conference on Artificial Intelligence (ECAI 2020)
ET-GAN: Cross-Language Emotion Transfer Based on Cycle-Consistent Generative Adversarial NetworksAIThe 24th European Conference on Artificial Intelligence (ECAI 2020)Despite the remarkable progress made in synthesizing emotional speech from text, it is still challenging to provide emotion information to existing speech segments. Previous methods mainly rely on parallel data, and few works have studied the generalization ability for one model to transfer emotion information across different languages. To cope with such problems, we propose an emotion transfer system named ET-GAN, for learning language-independent emotion transfer from one emotion to another without parallel training samples. Based on cycle-consistent generative adversarial network, our method ensures the transfer of only emotion information across speeches with simple loss designs. Besides, we introduce an approach for migrating emotion information across different languages by using transfer learning. The experiment results show that our method can efficiently generate high-quality emotional speech for any given emotion category, without aligned speech pairs.
@inproceedings{jianwei2020et-gan, title = {ET-GAN: Cross-Language Emotion Transfer Based on Cycle-Consistent Generative Adversarial Networks}, author = {Jia, Xiaoqi and Tai, Jianwei and Hang, Zhou and Li, Yakai and Zhang, Weijuan and Du, Haichao and Huang, Qingjia}, booktitle = {European Conference on Artificial Intelligence (ECAI)}, year = {2020}, } -
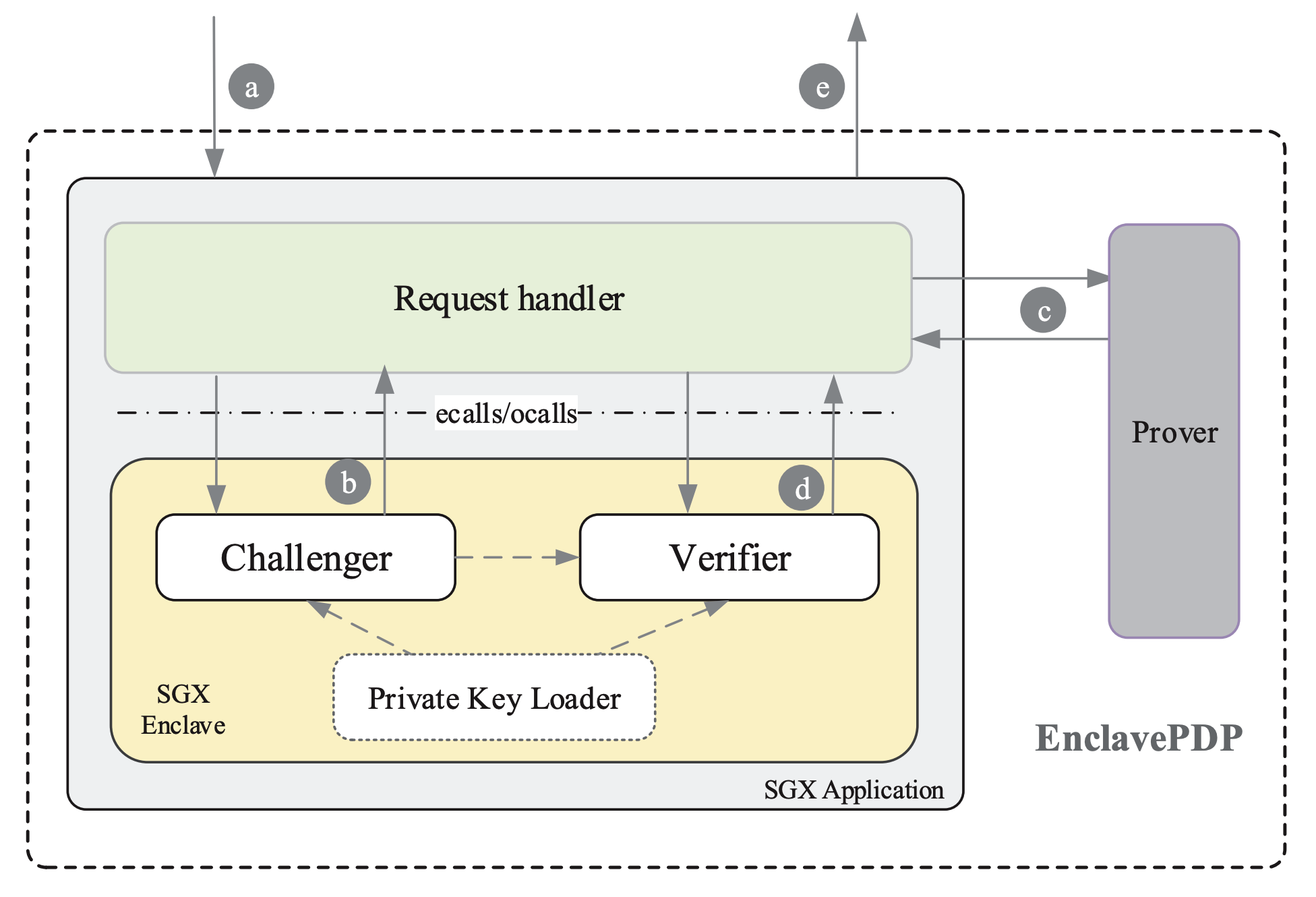 EnclavePDP: A General Framework to Verify Data Integrity in Cloud Using Intel SGXVirtualization TEE SGXThe 23rd International Symposium on Research in Attacks, Intrusions and Defenses (RAID 2020)
EnclavePDP: A General Framework to Verify Data Integrity in Cloud Using Intel SGXVirtualization TEE SGXThe 23rd International Symposium on Research in Attacks, Intrusions and Defenses (RAID 2020)As the cloud storage service becomes pervasive, verifying the integrity of their outsourced data on cloud remotely turns out to be challenging for users. Existing Provable Data Possession (PDP) schemes mostly resort to a Third Party Auditor (TPA) to verify the integrity on behalf of users, thus reducing their communication and computation burden. However, such schemes demand fully trusted TPA, that is, placing TPA in the Trusted Computing Base (TCB), which is not always a reasonable assumption. In this paper, we propose EnclavePDP, a secure and general data integrity verification framework that relies on Intel SGX to establish the TCB for PDP schemes, thus eliminating the TPA from the TCB. EnclavePDP supports both new and existing PDP schemes by integrating core functionalities of cryptography libraries into Intel SGX. We choose 10 existing representative PDP schemes, and port them into EnclavePDP with reasonable effort. By deploying EnclavePDP in a real-world cloud storage platform and running the 10 PDP schemes respectively, we demonstrate that EnclavePDP can eliminate the dependence on TPA and introduce reasonable performance overhead.
@inproceedings{yun2020enclavepdp, title = {EnclavePDP: A General Framework to Verify Data Integrity in Cloud Using Intel SGX}, author = {He, Yun and Xu, Yihua and Jia, Xiaoqi and Zhang, Shengzhi and Liu, Peng and Chang, Shuai}, booktitle = {23rd International Symposium on Research in Attacks, Intrusions and Defenses (RAID 2020)}, year = {2020}, isbn = {978-1-939133-18-2}, pages = {195--208}, publisher = {USENIX Association}, }